Figured I would make a thread to cover all the recent fun hacking/cybersecurity shit going on lately, especially after the Target/Adobe/{insert company here} breaches.
http://img.pandawhale.com/post-25067...Imgur-x71M.gif
University of Maryland:
http://blog.malwarebytes.org/hacking...ecords-stolen/
“A specific database of records maintained by our IT Division was breached yesterday. That database contained 309,079 records of faculty, staff, students and affiliated personnel,” Dr. Loh said. “The records included name, Social Security number, date of birth, and University identification number.”
I find it kind of funny, as they are one of the bigger competitors in MACCDC that my team is going to be competing against this year, and previous years. I can only assume the data going back to 1993 or w/e (reported elsewhere but couldn't confirm yet) is to keep track of alumni.
I'm curious if the data was encrypted in anyway (fucking lol if it wasn't) and what encryption was used/was the key compromised as well.
Guessing it was most likely a SQLi vulnerability, as that is usually 99.99% of the time the reason behind this sort of shit (input validation fuckers)
- Navigation
+ Reply to Thread
Results 1 to 20 of 666
-
2014-02-21 08:15 #1Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

The "Oh hey look who got hacked today" thread!
-
2014-03-18 19:56 #2Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

Off a twitter feed:
WhatsApp cares about privacy, so here's the AES key to decrypt all WhatsApp chats. 8D4B155CC9FF81E5CBF6FA7819366A3EC621A656416CD793
-
2014-03-18 20:07 #3Banned.


- Join Date
- Jun 2008
- Posts
- 6,675
- BG Level
- 8
- FFXI Server
- Phoenix

whaaaaaat
-
2014-03-18 21:03 #4Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

Posted that while walking out the door. Basically "can be used to decrypt the chat database that Whatsapp stores in the memory card of your android phone"
Whatsapp has been hit a lot on their privacy.
http://www.slideshare.net/segofensiva/bh-saopaulo
http://www.tomsguide.com/us/whatsapp...ews-18461.html
-
2014-03-18 21:05 #5Banned.


- Join Date
- Jun 2008
- Posts
- 6,675
- BG Level
- 8
- FFXI Server
- Phoenix

$17 Billion
-
2014-03-19 17:31 #6BG Content

EA games web server hacked
http://news.bbcimg.co.uk/media/image...4_73673243.jpghttp://www.bbc.co.uk/news/technology-13846031A web server belonging to the games company Electronic Arts has been hacked and is now hosting a phishing website, according to an internet security firm.
The website that has been put in place by hackers asks users to enter their Apple IDs - the credentials needed to access services like Apple's iTunes.
A second screen then asks users to enter further personal information, including credit card details.
EA said it was investigating the problem.
Paul Mutton, from Netcraft, the internet security company that uncovered the hack, said in a blog that it was likely a vulnerability in an online calendar application hosted on the web server had been exploited by the attackers.
The calendar based on the web server was an old version of software that had since been updated, he said.
"The mere presence of old software can often provide sufficient incentive for a hacker to target one system over another, and to spend more time looking for additional vulnerabilities," he wrote.
Once a user has entered their Apple ID and password on the fake website they are then asked to verify their name, date of birth, phone number and credit card details among other information.
Users were then directed to the legitimate Apple ID website, said Mr Mutton.
It was reported earlier in the year that other servers belonging to EA had been hacked, causing problems for users trying to log on to online games and services.
A hacking group known as Derp posted a tweet claiming responsibility for that attack.
Mr Mutton said he had reported the most recent problems to Electronic Arts but it appeared that the website still remained online.
In a statement to the BBC, EA said: "Privacy and security are of the utmost importance to us, and we are currently investigating this report."
Michael Sutton, from security research firm Zscaler, said that hackers using legitimate websites to host malicious content was now the norm.
"Social engineering attacks always involve an element of communication - the victim must be tricked into performing an action such as providing data, clicking on a link, downloading a file, et cetera. Attackers have learned that it's far easier to simply infect an already popular web property than to attempt communication with victims directly," he said.
Users should check that websites are secure before entering any private information, says guidance from Get Safe Online.
They should look for a padlock symbol in the browser window frame and they should check that the web address begins with https - the "s" stands for secure.
The advice also says that users should check the address in the browser's address bar after arriving at a website to check that it matches what they actually typed.
http://news.netcraft.com/archives/20...apple-ids.html
-
2014-03-21 08:02 #7Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

http://arstechnica.com/tech-policy/2...ud-conviction/
Wow, who would have thought that accessing a companies public webpage they never fucking secured would be like killing millions of people with a WMD.The government argued first, with Assistant US Attorney Glenn Moramarco telling the judges that Auernheimer's CFAA conviction should be upheld:
We have a case here where…[the defense counsel] is arguing that this was completely open to everyone. But you look at the testimony of Daniel Spitler and the steps he had to take to get to this wide open Web and I’m flabbergasted that this could be called anything other than a hack. He had to download the entire iOS system on his computer. He had to decrypt it. He had to do all sorts of things—I don’t even understand what they are.
Moramarco went on to equate Auernheimer's actions to blowing up a nuclear power plant in New Jersey.
In response, Auernheimer's lawyer Orin Kerr argued that visiting a public webpage does not constitute criminal "unauthorized access":
There is no unauthorized access in this case because of the nature of the World Wide Web. When you put information on the World Wide Web so that it’s available... you assume the risk that anyone will access that information. In this case, there was no private account information that was accessed. The only information that was collected was from public website addresses.
Kerr went on to suggest that in order for the CFAA to have applied in this case, there would need to have been some sort of “password-gate” or other way of keeping someone out, which was not present here. Kerr argued that Auernheimer did not hack into servers or steal passwords; rather, he discovered a major network security flaw at AT&T.
Also prosecutor doesn't even fucking understand what's going on.
Oh shit, he had to install an operating system?!...and decrypt the files? What, were they fucking using DES or a Cesar cipher/pig latin to encrypt this shit?He had to download the entire iOS system on his computer. He had to decrypt it. He had to do all sorts of things—I don’t even understand what they are.
-
2014-03-21 12:11 #8Chram

- Join Date
- Jul 2005
- Posts
- 2,582
- BG Level
- 7
- FFXIV Character
- Deejay Zombie
- FFXIV Server
- Excalibur

There is so much fuckin face palm in that article. Mr prosecutor if you dont know what the fuck he did or what this case is about maybe you should call an expert witness to explain it to you and the jury. Oh wait, if you did that you wouldnt have a fucking case. God damn any judge that knows anything about technology shouldve thrown this case out the minute thatn he was accessing a public unsecured websiten was brought up. Thats not fuckin hacking, thats typing a god damned web site address into your browser.
He made no effort circumvent security because there was none. Secure your data or assume someone will see it.
-
2014-03-25 09:59 #9Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

http://www.networkworld.com/news/201...-a-280030.html
Very cool piece of malware, especially since the mule can just pretend to be a regular ATM customer and not attract attention with a keyboard.The latest development was spotted by security vendor Symantec, which has periodically written about a type of malicious software it calls "Ploutus" that first appeared in Mexico.
The malware is engineered to plunder a certain type of standalone ATM, which Symantec has not identified. The company obtained one of the ATMs to carry out a test of how Ploutus works, but it doesn't show a brand name.
Ploutus isn't the easiest piece of malware to install, as cybercriminals need to have access to the machine. That's probably why cybercriminals are targeting standalone ATMs, as it is easy to get access to all parts of the machine.
Early versions of Ploutus allowed it to be controlled via the numerical interface on an ATM or by an attached keyboard. But the latest version shows a remarkable new development: it is now controllable remotely via text message.
-
2014-03-25 12:46 #10Caesar Salad

- Join Date
- Nov 2009
- Posts
- 28,355
- BG Level
- 10

That's some watchdog level shit. P.cool
-
2014-03-25 13:01 #11Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

Was also reading earlier today during lunch an article talking about "The Price of free Wi-Fi". Basically was talking about places like supermarkets, giving access to free wi-fi but with a EULA about storing the IP and MAC of any device that connects. Storing the IP doesn't mean shit, but storing your devices mac, most likely your phone, and logging into it will usually result in your phone auto-connecting each time you come to the store. Now if you have a "Perks" card that you use as well, they can slowly gather enough data of your MAC being in the store the same time your card was swiped and begin to track your shopping habits based solely on your device instead of just the card which people sometimes don't use.
Was interesting, and then I noticed this that a London group has made.
http://www.mirror.co.uk/news/technol...k-your-3280351
Basically a UAV that uses "Evil Twin" AP attack.Drones, once just used by the armed forces, are now used for everything from delivering cold beer to fishermen to taking photographs of reindeer as the civilian market booms.
The Snoopy drone is the latest example and it presents a different kind of threat- to your personal data.
The device, which can hack into smartphones and steal users' information, shows how vulnerable phones are to hacking.
Sensepoint security, based in London, developed the hacking device which searches for mobiles which are trying to connect to a wifi network.
Phones remember previously used networks which the snoopy application exploits by tricking your phone into thinking it's a network you've used before.
I'm curious as to how it gains knowledge of the networks that your phone "Remembers", guessing it broadcasts that to some extent while searching for an AP?
-
2014-03-28 07:50 #12Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

Facebook social engineering: Steal yourself a girlfriend!
http://andrew.codeusa.net/post/80965...-your-facebook
Final Thoughts
On most trials a link was received which gave direct access to the victims account, but on occasion I had to recover the password using the phone number which had been added to the victims account. In both cases access was gained quickly.
From there on out you have access to the account, even if they remove the phone number there is a grace period where I can continue logging in and adding the number back. Changing the password does nothing.
I informed facebook about this exploit 3 weeks ago when I found it, as of posting this it has still not been fixed.
But at least they replied
Hi,
Your report appears to describe a social engineering or spam attack against Facebook users and infrastructure. Although we appreciate the report, such issues do not qualify under our bug bounty program.
Neal
Security
Facebook
A few things could be done to easily fix this:
-
2014-04-09 07:11 #13Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

http://heartbleed.com/
Reading memory of another machine through the internet! awwwwww yeah.The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet. SSL/TLS provides communication security and privacy over the Internet for applications such as web, email, instant messaging (IM) and some virtual private networks (VPNs).
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.
Code samples of the bug:
int
dtls1_process_heartbeat(SSL *s)
{
unsigned char *p = &s->s3->rrec.data[0], *pl;
unsigned short hbtype;
unsigned int payload;
unsigned int padding = 16; /* Use minimum padding */typedef struct ssl3_record_st
{
int type; /* type of record */
unsigned int length; /* How many bytes available */
unsigned int off; /* read/write offset into 'buf' */
unsigned char *data; /* pointer to the record data */
unsigned char *input; /* where the decode bytes are */
unsigned char *comp; /* only used with decompression - malloc()ed */
unsigned long epoch; /* epoch number, needed by DTLS1 */
unsigned char seq_num[8]; /* sequence number, needed by DTLS1 */
} SSL3_RECORD;/* Read type and payload length first */
hbtype = *p++;
n2s(p, payload);
pl = p;unsigned char *buffer, *bp;
int r;
/* Allocate memory for the response, size is 1 byte
* message type, plus 2 bytes payload length, plus
* payload, plus padding
*/
buffer = OPENSSL_malloc(1 + 2 + payload + padding);
bp = buffer;Taken from here: He also has info on what is going on in the code and why the bug exists (aka stop trying to build secure shit in C)/* Enter response type, length and copy payload */
*bp++ = TLS1_HB_RESPONSE;
s2n(payload, bp);
memcpy(bp, pl, payload);
http://blog.existentialize.com/diagn...bleed-bug.html
-
2014-04-11 09:20 #14Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

http://www.ibtimes.com/google-chrome...ations-1569646
All it takes isA security flaw in Google Chrome, currently the world's most popular Web browser, could allow a hacker to turn on a user's computer microphone and secretly obtain a Chrome-generated transcript of the user's conversations, according to an Israel-based software developer who highlighted the flaw in a blog post this week.to access the users speechCode:<input -x-webkit-speech="" />
Website used for demonstration
http://guya.net/security/speech/
-
2014-04-11 13:29 #15I'll change yer fuckin rate you derivative piece of shit

- Join Date
- Sep 2006
- Posts
- 55,091
- BG Level
- 10

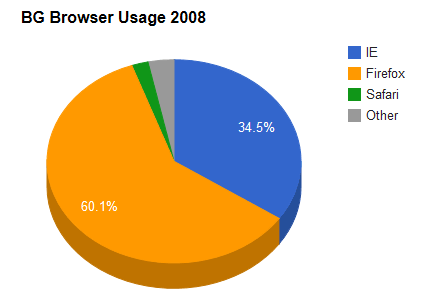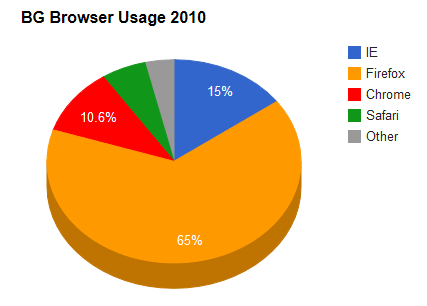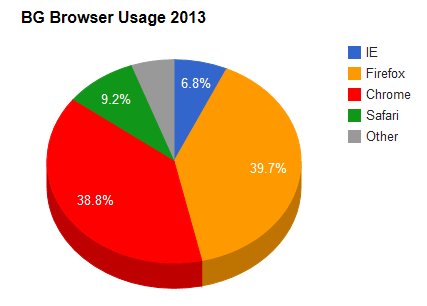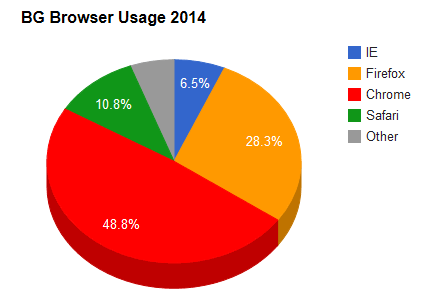
When the fuck did Chrome become the most popular web browser - I was sure that was wrong, but wikipedia backs it up.
Man I thought people were still being tech-illiterate dinosaurs with IE as their main...
-
2014-04-11 16:03 #16Ridill

- Join Date
- Jul 2008
- Posts
- 9,495
- BG Level
- 8

-
2014-04-11 21:49 #17Bagel

- Join Date
- Jan 2009
- Posts
- 1,414
- BG Level
- 6

Heartbleed has been a lot of fun. Not really. Changed out all my certs finally, still some loose ends to tie up. I still use IE for testing, but I bounce back and forth between Torch and Firefox as mains.
-
2014-04-13 17:30 #18Pay No Attention to the Man Behind the Curtain


- Join Date
- Dec 1969
- Posts
- 3,566
- BG Level
- 7
- FFXIV Character
- Ragns Meuhie
- FFXIV Server
- Gilgamesh
- FFXI Server
- Bahamut
- Blog Entries
- 144
-
2014-04-13 19:26 #19The Shitlord

- Join Date
- Feb 2008
- Posts
- 11,366
- BG Level
- 9
- FFXIV Character
- Kharo Hadakkus
- FFXIV Server
- Hyperion
- FFXI Server
- Sylph
- WoW Realm
- Rivendare

eagerly awaiting the news that Google has merged with Wal-Mart and renamed themselves Buy-N-Large
-
2014-04-13 23:55 #20Mr. Anna Kendrick

BGs Worst Golde Abuser
- Join Date
- Jul 2007
- Posts
- 10,974
- BG Level
- 9
- FFXIV Character
- Charles Barkley
- FFXIV Server
- Faerie
- FFXI Server
- Quetzalcoatl

My work still uses IE9 and we require our subcontractors to use IE10 even though we dont have it installed LOL
 XI Wiki
XI Wiki



 Reply
Reply